A "low and slow" approach to financially driven cyber attacks has overtaken ransomware as the chief attack vector as criminals seek to extort money b
Read MoreThanks to a massive paradigm shift in the way business is conducted, companies rely more and more heavily on digital environments every day. But
Read MoreIT organizations are largely siloed between the desktop and mobile management worlds. IT has addressed management of mobile devices with modern e
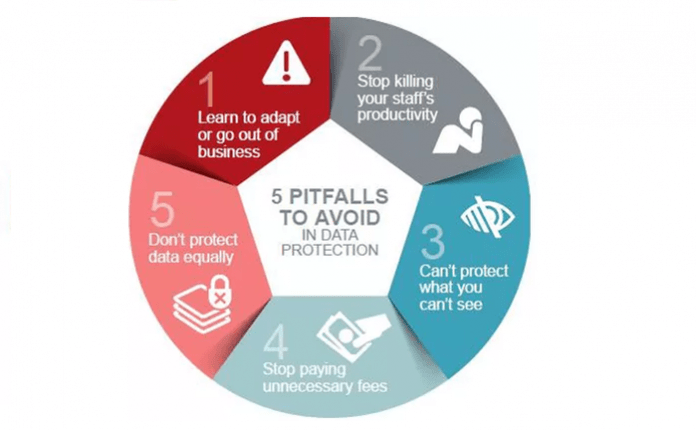
Read MoreToday, organisations have very little visibility into their data infrastructure, unable to discern what data is important or not. This creates si
Read MoreOffice 365 is a security-hardened service, designed following the Microsoft Security Development Lifecycle. We bring together the best practices
Read More